02 April 2008
Speed Up Your PC in 3 Easy Steps, Part II
In the spirit of last month's Tech Tip of the Week touting several handy open source utilities available for free on the internet, here is a revision of The Three Steps that uses some excellent third-party applications that won't cost you a dime.
CLEAN.
Disk Cleanup is a basic Windows utility that deletes files off your hard drive that Windows knows you don't need anymore. CCleaner is a free utility that does that same cleaning job, then takes the Lysol to several other sludgy corners of your hard drive. It goes into your browser (including Firefox and Opera) and cleans out your browsing history and
cookies. It examines your Windows Registry and remove unused and old entries, often a source for slow system performance. (Wisely, CCleaner backs
up your registry before it begins tinkering with it.) It even examines some of your third-party applications and removes known temporary files. CCleaner gives you the ability to select exactly which of these things to search for and delete, so you have granular control over how far you want to scrub your hard drive.
In my testing, I've found the application to work as advertised. I have yet to encounter an installation or cleaning run that caused ostensible registry issues or application problems.
When you download and install the application, I recommend you check/uncheck the following boxes on the Install Options dialog box:
CHECK: Add Desktop Shortcut
CHECK: Add Start Menu Shortcuts
UNCHECK: Add 'Run CCleaner' option to Recycle Bin context menu
UNCHECK: Add 'Open CCleaner...' option to Recycle Bin context menu
CHECK: Automatically check for updates to CCleaner
UNCHECK: Add CCleaner Yahoo! Toolbar and use CCleaner from your browser
A final note on CCleaner: I have to give special props to a program that was originally distributed as "Crap Cleaner", but ended up shortening its name as a result of its popularity.
DEFRAG.
The disk defragmentation program built into Windows XP is fairly lame. Many people suspect it is no different than the Disk Defragmenter that was shipped with Windows 95 nearly thirteen years ago. Windows Vista's version of Disk Defragmenter is actually worse than the one in Windows XP. Gone is the nice graphical map of your hard drive's contents, showing an up-to-the-second diagram of the fragmented files on your drive. (In fact, you don't even get a progress bar...the utility just says "Hey, I'm defragging now. I'll let you know when I'm done.") Both versions are painfully slow and often don't do a complete job.
AusLogics Disk Defrag is a nice alternative. The program works quickly, gives you a nice diagram of the disk contents and the defragmentation at work, and sports a reliable progress bar. After defragmentation, you get a quick summary of the defragmentation and it gives you the option of viewing a detailed report in your browser.
The application also notifies you of so-called "junk files" on your hard drive that you should remove. This is little more than an ad, directing you to purchase AusLogics' BoostSpeed application for $30 from their website. A minor
annoyance, but worth it considering the utility of the free Defrag app.
PREVENT.
In my original "Clean, Defrag, and Prevent" Tech Tip, I mentioned setting up your browser to prevent the accumulation of temporary internet files.
Let's expand the scope of this "Prevent" step to include the prevention of malware on your PC. All Windows PCs should have antivirus, antispyware, and a software firewall installed for maximum
prevention against cyberthreats. And as I described back in February, some of the best security software is absolutely free. Installing and running security software can pay immediate dividends by eliminating malware that hogs your PCs resources. The long-term security gains are less concrete but no less important: information privacy and peace of
mind.
Make The Three Steps a regular routine! If you clean and defrag every few months and ensure you're preventing malware, you can be confident you're always using a healthy PC.
12 March 2008
The Best Things in Life Are.......Open Source!
Open source software is software that is not only free, but who's "ingredients" are open to the public. It cannot be owned by any person or organization; rather, it is freely "owned" by the community of computer users that we are all a part of. By keeping the inner workings of the software (the "source code") open to everyone, people are all welcome and encouraged to modify and improve upon that source code. The only stipulation is that if you improve or modify the code, your version of the source code must also be open to the public.
Thus the name "open source", as the source code is open to all for use and modification. It's sort of a groovy, communal approach to software development. Staunch capitalists might scoff at the concept, but it is the reason why great public domain websites such as Wikipedia.org are so successful. We all "own" Wikipedia, and by opening its contents to everyone in the world, we all can expand and refine it for the common good. Maybe hippie ideals finally have found their day in the sun, albeit 40 years later.
At any rate, like Wikipedia, there are great pieces of software out there that just so happen to be open source. Think that a lack of corporate oversight and capital incentive makes for an inferior product? Think again! These days, there are some open source applications that are as good or better than similar commercial software applications.
I'd like to make you aware of several that I've come across. Don't be fooled by the lack of a price tag on any of them. In this day and age, at least on the internet, sometimes the best things in life really are free.
OpenOffice
www.openoffice.org
Open source or not, OpenOffice is the most popular alternative to Microsoft Office, period. Some now even claim that OpenOffice is superior to the Microsoft product (which can retail for as much as $500). The OpenOffice website boasts that OpenOffice is "...simply better software for writing...drawing...spreadsheets...presentations...information."
Regardless of how close it has come to Microsoft Office in terms of functionality, if you can't afford to buy Microsoft Office for home use, you should absolutely install OpenOffice instead. One word of caution, however: while OpenOffice can open many Microsoft Office files at home, you may have difficulty opening OpenOffice files with MS Office applications at work.
Paint.NET
www.getpaint.net
I dedicated an entire Tech Tip to this one last year, actually.
PuTTY
www.chiark.greenend.org.uk/~sgtatham/putty/
My web host let me know about this one a few years back. At the time, I was in need of a Telnet client that uses the SSH protocol. What I ended up with was this suite of tools (including a secure FTP client) that are open-source, clean, and stable. While the FTP client isn't graphical (you'll need to know the text commands), it is handy when you're away from your home computer and need a quick-and-dirty FTP client for file transfers.
From the main page, click Download. Then on the Download page, select the EXE file below "A Windows installer for everything except PuTTYtel". This is the full suite, and the version you want.
Firefox
www.mozilla.org
In last month's "Security Dance" Tech Tip, I mentioned two of the top free web browsers. One of the two, Firefox, is also open source. Spearheaded by The Mozilla Foundation, Firefox is the second most popular browser on the internet (trailing only Internet Explorer). Fans of Firefox rave about its superior security features, improved performance, and rich feature set when compared with Microsoft's ubiquitous browser.
Thunderbird
www.mozilla.org
Also part of the Mozilla Project but lesser known is Thunderbird, an open-source mail client similar to Microsoft Outlook. According to the Mozilla website, Thunderbird boasts "...safe, fast, and easy email, with intelligent spam filters, quick message search, and customizable views." If you are annoyed with Microsoft Outlook Express on your home PC and don't have the money (or the patience) to install the full Microsoft Outlook, consider this app.
Audacity
audacity.sourceforge.net
Ardour
www.ardour.org
Are you a starving musician who wants to record and edit music at home, but doesn't have the scratch to even buy new guitar strings? Or maybe you're a regular schlub who just wants a simple, clean MP3/wave file editor for putting together audio clips for a slideshow?
If you're the former, then Ardour is for you. You are already aware that "digital audio workstation" (DAW) suites like Pro Tools, Cakewalk SONAR, Cubase, and Logic costs hundreds of dollars. Luckily for you, an organization of people has been developing an open source alternative to these industry goliaths for several years now. As DAW suites are extremely sophisticated and hard to duplicate, it is impressive that anyone would attempt to create an open source DAW. I have not had the chance to check out Ardour myself, but from what I've read about it, industry folks are impressed with it. While it may never reach the level of popularity, prestige, or even functionality of Pro Tools, Ardour is absolutely worth a look by anyone who wants to set up a home studio on a budget.
If you're the latter, then you should download a copy of Audacity. This application edits single MP3 and WAV files much the same way Sony's Sound Forge application does. A rich set of features from the simple (cut-and-paste, fade in/fade out) to the more specialized (pitch shifts, normalize, compression, reverbs, wah-wah, flange, etc.) are all available. Using both applications side by side, I have found Audacity to be a stable and fairly intuitive alternative to Sound Forge. Audacity also made CNET's "The 10 Best Downloads of 2007".
EXTRA TIP: If you decide to check out Audacity, after you download and install the application, you will need to install an additional file called "lame_enc.dll". Click here for instructions on downloading and installing this file.
Pidgin
www.pidgin.im
Also listed as one of CNET's "10 Best Downloads of 2007" is this handy app. If you're someone who likes to do instant messaging over the internet with AOL Instant Messenger (AIM), ICQ, MSN Messenger, Windows Messenger, Yahoo! Messenger, IRC, or one of the litany of other chat clients, you might consider switching to this one. With so many different chat clients and protocols in existence, it may be impossible to get all of your friends onto one platform. Pidgin works with all of them. Simply enter your account information for each of your chat clients and Pidgin lets you chat on all of them at the same time. There are other multi-platform chat apps available on the 'net (Trillian is the one I've used in the past), but this is the first open source application I've seen to offer the same functionality.
SmoothWall
www.smoothwall.org
Here's an interesting idea: take an old PC that you're not using anymore, even if it's an old Pentium II, and turn it into a robust hardware firewall to protect your entire home network. Sounds like a good idea if the firewall software is $80. Sounds like a great idea if the software is open source! Kudos once again to CNET for the great tip.
Linux
www.knoppix.org
www.ubuntu.com
www.fedoraproject.org
www.opensuse.org
Last but certainly not least is the most famous open source software of them all, and the biggest threat to Microsoft's operating system (OS) monopoly: Linux. Those who like Linux love it. Those who dislike Linux tend to compare it and its predecessor Unix to the homophone of Unix. Switching from Windows to Linux is a practical, philosophical, and even cultural change akin to converting from Christianity to Buddhism. Not only will you be disconnecting yourself from most of the applications and system tools that you and almost everyone else uses daily, but you are effectively choosing to limit your support base to a relatively small number of people who actually know and understand how it works.
But nobody says you can't dabble in the Zen world of Linux in your spare time even if you're a slave to Windows during the work week. After all, Linux doesn't cost anything to download or install. If you have multiple PCs at home, why not install Linux on one of them and see what all the excitement is about? In fact, erasing an old, plodding Windows PC and installing a fresh copy of Linux on it might breathe new life into it. Some versions of Linux (referred to as "distributions") run substantially faster than Windows, and can make an antiquated PC run nearly as fast as a brand-new one does on Windows Vista.
There are many different distributions of Linux available. I included four of the most common in the links above.
Knoppix is the best for a total newbie who simply wants to see what Linux looks like. What's unique about the Knoppix distribution is that you can get it as a bootable "operating-system-on-a-CD-ROM". Simply create your own Knoppix CD, then boot your computer off of it to load the Knoppix Linux OS into memory. When you're done, pop the CD out of the drive and reboot. You can explore a full-blown version of Linux right on your own computer without installing it or changing anything on your hard drive!
When you're ready to reformat a computer and do a fresh operating system install, consider one of the other three: Fedora, openSUSE, or Ubuntu. Each distribution has its own pros and cons; only the most devout Linux-heads will be able to elucidate the differences for you. But hey: you can't learn how to swim unless you get in the water! If you take the plunge with one of these three, at least you'll know you're working with one of the most popular versions of Linux available.
05 March 2008
For SysAds: Deploying Enterprise Vault
After much work, this is the procedure that we came up with. Keep in mind that almost none of our users were running Cached Exchange Mode, a prerequisite for EV, prior to the rollout. Here it is, for those of you who may be looking to roll out this system to your company or organization...
How to Roll Out Symantec Enterprise Vault
1.
Make sure all of your clients have at least MS Office Service Pack 2 installed.
2.
Create two user-based group policy objects called “Enable Cached Exchange Mode” and “Disable AutoArchive”.
The first one should look like this.
Note that this GPO calls a login script. You can find a version of this script here, including an excellent explanation of what it does and how to use it.
The second one should look like this.
Once you have these GPOs set up, apply them to your user accounts.
3.
Try to give as much time as possible between steps 2 and 3. You need to ensure everyone gets the Enable Cached Exchange Mode policy before hitting them with the next policy. (See Notes section below for more info on this.)
Once everyone is running Cached Exchange Mode, create a computer-based GPO called “Install EV 2007 Client Exts”. It should look something like this.
Once it is set up , apply this GPO to the appropriate computers.
4.
Ensure Use mailbox store defaults is checked off under the "Exchange General" tab in Active Directory for each of your users.
If you have a lot of users with non-standard mailbox sizes, use this handy tool to make bulk changes. I like it. Actually, it's a nice tool for making all sorts of bulk changes to Active Directory objects. But I have verified that it does work specifically for the "Use mailbox store defaults" switch.
Also, if you're unsure which of your users have non-standard mailbox limits, here's a handy script we found. According to its author, it "lists all mailboxes that have their limits changed to bypass store defaults (mDBUseDefaults=FALSE), and lists the 3 attributes above if present."
5.
After all the client extensions are installed, add the user to the security group set up in Active Directory specifically for your Enterprise Vault users. (You would have created this security group when you first installed EV on your Exchange server.) This lets the message server know that this user needs to be “vaulted”. The account will get added to EV sometime in the next 24 hours, depending on what you specified in your EV installation.
Notes
• If any clients aren't on Cached Mode when you install the Outlook Client Extension on them, their Outlook will stop working. They will get an error message when starting up Outlook, then the application will close. If this happens, you will have to manually set up Cached Mode for them to fix the problem: go to Control Panel, select Mail, click on E-mail Accounts, click Next >>, click Change..., and select Cached Exchange Mode.
• Make sure your users know they can’t use the Archive feature of Outlook anymore. AutoArchive will now be shut off, but if they try to manually archive messages that are already archived by EV, they will be unable to open those messages.
27 February 2008
The Security Dance
You may not even know how to answer this question, given all the different types of security threats that all internet-connected computers face these days. PC security is more than a state of mind -- it's doing everything you can to protect yourself from people who want to hijack your computer, damage your data, and steal your personal information.
There are three key pieces of security software you need to have on your home computer:
ANTIVIRUS
ANTISPYWARE
FIREWALL
You may own one piece of software that accomplishes all 3 functions such as Norton Internet Security. Regardless, take the time to examine the security software you have installed on your PC. You may be leaving a gaping hole open to cybercriminals.
Here are some common pitfalls for home users, as well as some easy solutions.
1. Having antivirus software with no antispyware, or vice versa.
Once upon a time, all home users needed was antivirus software to ensure security. That was 10 years ago. Today, viruses may be the least of our threats. Adware and spyware can cripple a PC's resources and gather personal information about users. Some antivirus software applications have antispyware capabilities (and vice versa), but even those applications fall short in spyware detection.
A firewall, on the other hand, will protect you from live threats. There are lots of automated systems out there "sniffing" around, pinging random web addresses looking for an open hole into someone's computer. An "intrusion" into your system might even originate from deliberate human hacking. You need a firewall to shield your system from this hailstorm of attacks. A good firewall will not only tighten up all open network ports on your PC against incoming riff-raff, but it will scrutinize all outbound network traffic as well. That way, if adware or spyware on your PC tries to send data to a host site, the firewall will block this activity.
Adware, spyware, viruses, trojan horses......so many terms. There is one word that encompasses them all: malware. The best way for home users to protect themselves from malware is to install dedicated antivirus and anti-spyware and firewall software.
2. Relying on Windows Firewall as your sole firewall.
Windows XP and Vista both come with a rudamentary firewall as part of the operating system. While well-intentioned and not harmful for most home users, the efficacy of Windows Firewall is lame at best.
The best practice is to keep Windows Firewall enabled on your PC but install an additional software or hardware firewall for your system.
3. Letting the subscription expire on your security software.
Sure, you've got McAfee Antivirus and Trend Micro Antispyware software installed on your PC. No worries, right? Well, have you checked to see if your subscription is still active? It's important to keep your security software updated with the most up-to-the-minute malware information. Once the subscription expires, your security software will continue to run, but it will fail to detect the latest threats.
Open up each of your security applications and verify the expiration dates. You might want to make a note to yourself (perhaps an Outlook calendar appointment?) to renew your security software subscriptions right before they expire.
4. Ignoring security software because you're broke.
Hey, I get it. Antivirus costs $30, antispyware costs $30, and the firewall software might not even be included.
While there are many excellent commercial applications available, you can actually get decent protection without spending a dime. Here are a number of absolutely-free security applications:
ANTIVIRUS
- AVG Anti-Virus Free Edition
- Avast Home Edition 4.7
- Avira AntiVir PersonalEdition Classic
- PC Tools AntiVirus Free Edition 4.0
- Ad-Aware 2007
- Microsoft Windows Defender
- SpyBot Search and Destroy 1.4
- Trend Micro HijackThis 2.0.2
- SpywareBlaster 3.5.1
- Spyware Terminator 2.1
- AVG Anti-Rootkit (for Windows XP only)
Download and install any single application from each of the three categories if you don't have any protection. And don't be afraid to install more than one antispyware software at a time -- you can run multiple. Studies have shown that different antispyware applications catch different pieces of malware, so the more antispyware software you have installed, the greater your chances are complete protection.
5. Downloading from websites you haven't 100% verified.
You should know not to download anything from the internet unless you've verified the source. Even well-intentioned websites can carry infected software for download. Other websites are "spoofed", making you think that you're on a trusted site when in fact you're on an identical fake, feeding you malware and collecting your information.
Take the time to type in the exact address of the website you want up in the address bar of your internet browser. Sometimes simply doing a Google search for the website that you want yields spoof sites!
Also, avoid downloading and installing unnecessary software. But if you must, download it from a trusted, secure website such as http://www.download.com/ or http://www.pcworld.com/.
6. Using Internet Explorer, particularly versions 5 and 6.
Right, I know that the grand majority of internet users surf the web with some version of Microsoft's ubiquitous Internet Explorer. (Over 70% of you who visit my website use IE.) I'm not going to lie: I happen to be using it right now. There are websites that won't work correctly without it.
The problem is that all the criminal hackers in the world also know that 70% of you use IE. And that one fact makes IE a prime target for hacking.
Microsoft makes a decent attempt at trying to patch the security holes in IE, but the fact remains that a browser this popular is simply too big a target for hackers to find holes in. Although security patches come out on a regular basis from Microsoft (and you should always install them -- more on this below), they appear to be falling further and further behind in the cat-and-mouse game of browser security.
Fortunately, two of the best alternative browsers are free of charge: Mozilla's popular Firefox browser, and Opera Software's Opera Browser.
Why not give one of them a try? It only takes 5 minutes to download one of them, import all of your IE bookmarks into the new browser, and start surfing. You don't have to commit to using either of them permanently, and you can still run IE if you need to -- even simultaneously with Firefox or Opera. You may also notice a slight increase in browsing speed over IE, although I have not been able to verify this on either browser.
7. Not installing all the latest Windows Updates.
Microsoft Windows XP is still a work-in-progress, even as it approaches 7 years of age. (Windows Vista is more like a work-in-gestation!) It requires regular updates and patches from Microsoft to keep it as stable and secure as possible. Fortunately, Microsoft has automated this process for you. To ensure that you get regular updates, do the following:
- Right-click on My Computer and select Properties
- Select the Automatic Updates tab
- Ensure that the first option is selected: Automatic (recommended)
- Click OK
When new updates are automatically downloaded by your computer from the Microsoft website, a yellow shield will appear in the lower-right corner of your screen:
 Click on it! A dialog box will then ask you if you want to install updates. Say yes! The updates will begin to install themselves. You may be required to restart your computer at the end of this process.
Click on it! A dialog box will then ask you if you want to install updates. Say yes! The updates will begin to install themselves. You may be required to restart your computer at the end of this process.You can also manually verify that your computer is completely up to date:
- Go to the Start and select All Programs
- Select either Microsoft Update or Windows Update
An IE window will pop up that will take you to a special Microsoft website that checks your PC for installed updates. Follow the on-screen instructions to determine if your PC needs additional Windows updates.
20 February 2008
For SysAds: Symantec Enterprise Vault
So I wrote one from scratch. Here it is, for those of you who may be looking to roll out this system to your company or organization...
In the next few days, we will be rolling out Enterprise Vault, a system that will give you a large additional space (an archive) for storing email. You will need to actively maintain this storage space (the "vault") to ensure that you do not exceed the 450 MB limit. Be aware -- it's easier to reach your limit than you think!
Enterprise Vault works automatically, but there are seven important things you need to know about the changes it will make to Microsoft Outlook on your PC:
1.
All emails that are more than 2 weeks old are automatically archived into the vault. You will still see the emails in your inbox list, but the icon will look different:
2.
If you select one of these archived messages, you'll notice that the message preview in the Preview Pane will be limited to the first 500 characters of text, with no attachments:
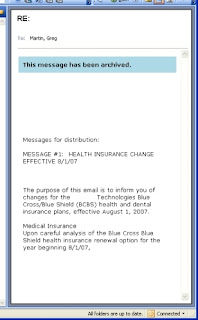
Also note the text in the blue box stating "This message has been archived."
3.
If you want to access the entire message and its attachments, simply double-click on the message. You will need to wait several seconds for the message to load from the Enterprise Vault archive.
If you need to open this message frequently, you can move the message permanently out of the vault back into your inbox. Simply highlight the message in your inbox and select the "Restore from Vault" button in your Outlook Toolbar:
 Then a dialog box will pop up....just click the OK button:
Then a dialog box will pop up....just click the OK button: 
4.
If you wish to delete a message that has been archived, a box will pop up when you delete it:
5.
You can store any message you want into the vault. Simply highlight the message and click the Store in Vault button on your Outlook Toolbar:
 Consider using Enterprise Vault instead of your Personal Folders to store your messages! Unlike Personal Folders, Enterprise Vault uses Outlook Web Access, gets backed up frequently, and is far more crash-proof and corruption-proof.
Consider using Enterprise Vault instead of your Personal Folders to store your messages! Unlike Personal Folders, Enterprise Vault uses Outlook Web Access, gets backed up frequently, and is far more crash-proof and corruption-proof.6.
Your vault is completely searchable. Click on the Search Vaults button:
7.
Enterprise Vault works the same way as above when you are checking your email at home or on the road using Outlook Web Access. The buttons, icons, and functionality are all the same, except when you want to Search Vaults, click the Search Vaults button on the bottom-left of your internet window:
13 February 2008
Coming Up With a Password
The requirement? The password must contain both capital and lowercase letters. And numerals. And symbols! And it can't contain any common "dictionary" words!! You find yourself sitting in front of the "Change Password" dialog box for 30, maybe 40 minutes trying to come up with a password that the system will accept as "strong".
Finally, you give up. "I'll just use a bunch of random letters, numbers, and characters," you say. Except that the next day when you try to log in, you can't remember your cryptic password, which was "5Hg&T#f90p@!1". And then again a week later you forget. And then again a week after that you forget, and your IT guy is about ready to strangle you.
There are easier ways to meet the criteria for a strong password. Here are some ideas that you can use to come up with unique, strong passwords that you can remember. You'll note that there is a common theme among all the ideas: the key is to come up with something familiar that contains both letters and numbers!
1. How about a song that contains both letters and numbers? Perhaps you're a big fan of 'hair bands', particularly Poison, and "7 Days Over You" is one of your favorite album tracks. Simply run the words together (keeping the capitalization) and put a character at the beginning or end of it:
- #7DaysOverYou
- 7DaysOverYou$
- *7DaysOverYou
2. How about a town and zip code that you once lived in, or of a relative or friend? The benefit here is that most city/town names aren't common dictionary words, so they usually meet the strictest password criterias. Here are a few examples:
- @SedonaAZ86339
- TacomaWA98402%
- Krumsville,PA19534
3. Maybe there's a car you once drove? Or one you dream of owning?
- 1971PlymouthCuda!
- 91PontiacTransSport&
- (88HondaCivicCRX)
4. On extremely tightened-down systems, the above suggested passwords still aren't strong enough. Something you can do to make these passwords even stronger is substitute numerals and symbols for similar-looking letters. By doing so, you can take even a fairly weak password like "Carrots" and turn it into a strong password like "C@rr0+$". Here are some classic numeral and symbol substitutions:

The key is to make a password that you can remember. If you use your first car as a password and the password expires, move on to the second car that you owned, then the third. That way, if you forget the following day that you changed your password, it will only take you one or two more attempts to remember what your new password is. (Most systems only allow 3 attempts before your account is locked up, so this is important.)
If you use ideas like the ones above, you can easily create strong passwords that you won't have to tape to the underside of your keyboard!
06 February 2008
For SysAds: Removing "XPS Document Writer"
Since then, I've discovered that it may be best to also remove the Document Image Writer's equally-annoying younger brother: Microsoft XPS Document Writer.
XPS (XML Paper Specification) is Microsoft's latest alternative to PDF. Your organization may or may not be using it, so the first thing to do is find out if your users are. The odds are that they aren't: like it or not, PDF is here to stay for a while. Microsoft often tries to create alternate formats in an effort to increase market share (see: WMA audio files and WMV video files), but these proprietary formats are not always successful.
If none of your users create XPS files or use the XPS Document Writer, then you may want to consider removing Microsoft XPS Document Writer from all user profiles. It tends to cause the same issues as "Image Writer" when a user doesn't have any printers set up or has the wrong printer set as the default. (See my previous article linked above.)
To remove all XPS Document Image Writers from all user profiles at logon, simply add these 3 lines of code to your user login script (or create one for this if one doesn't exist):
You can delete or "rem out" this line of script once it's been run by all your users.c:
cd \windows\system32\
cscript prnmngr.vbs -d -p "Microsoft XPS Document
Writer"
30 January 2008
For SysAds: WSUS Tips
-=-=-=-=-=-=-
- In the group policy object (GPO) that you created for WSUS, go to Computer Configuration/Administrative Templates/Windows Components/Windows Update and make sure you have enabled the option "Enable client-side targeting". Then create a "Target Group Name" for that WSUS server:
- In the WSUS 2.0 console, under Options / Computers, change to the other option: "Use Group Policy or registry settings on computers" to specify how to assign computers to groups. In WSUS 3.0, go to Options in the left pane, then Computers, and select "Use Group Policy or registry settings on computers":
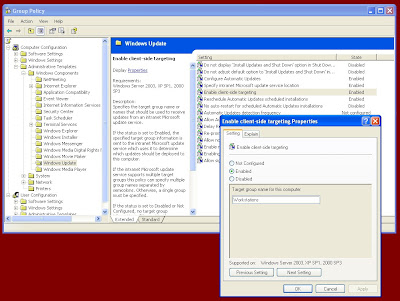

Now it will pick up all domain computers that receive your WSUS GPO...and have the most updated version of Windows Update client installed. So if you find that there are still some workstations out there that aren't getting picked up by WSUS, and you know that they're getting the GPO, then you need to update Windows Update client (wuauclt.exe) on each of them.
The simplest way to do this is:
- Log into that machine as an admin, right click on My Computer and select Properties.
- Click on the Automatic Updates tab, then click on the text towards the bottom of the window that says Windows Update Web site. (On a Vista workstation, click Windows Update in the bottom left of the window, then click on the text that says Get updates for more products.)
- The Windows Update website pops up. The first thing it does is check to see if you have the most current version of Windows Update client installed on your PC. Allow it to run this check and accept all recommendations for updates. If it asks you if it can install something, click Install or Install Now. You may need to allow it to run an ActiveX control first.
- When you see "Welcome to Windows Update", you know that you now have the latest version of Windows Update client installed. (On Vista workstations, you will see "Microsoft Update was successfully installed.")
- The website may suggest that you upgrade Windows Update to Microsoft Update. You can do this too, as it provides the ability to update other Microsoft software such as Office, but it is an optional step in this process.
Hopefully, after all this, your WSUS server will finally see all of your workstations.
But if not, you've got one last shot. Go to the workstation that your WSUS server can't see and do the following:
- Open up a DOS window and at the prompt, type in: wuauclt.exe /detectnow This forces the WSUS server to detect this workstation right away.
- Or if that doesn't work, try wuauclt.exe /resetauthorization /detectnow According to Microsoft, this "expires" the local cookie that it gets from WSUS and then phones home.
-=-=-=-=-=-=-
Speaking of wuauclt.exe, there are apparently a number of undocumented switches that you can use with wuauclt.exe at the command line. If this interests you, you can read more about them here.
-=-=-=-=-=-=-
Finally, a word of advice about how to deal with WSUS to update your servers. Many SysAds are afraid to use WSUS on their servers because it has been known to automatically reboot servers once approved patches are applied. There are plenty of horror stories like this on the web; certainly, you don't want your production servers rebooting in the middle of a business day or during a backup, and obviously you don't want servers rebooting without prior scheduling and notice to your users.
The problem is that even with the "No auto-restart" toggle enabled in the WSUS GPO, servers can still automatically reboot under certain circumstances. This toggle will only prevent auto-restart if a user is logged in. If no user is logged in (typical for servers), then it will still auto-restart.
This is how you can use WSUS to update your servers without fear of auto-restarts:
- Make a completely separate WSUS GPO for your servers. (I actually have set up separate WSUS GPOs for "Test Servers" as well, so that Server 2003 patches can be tested on non-essential servers before patching them to production servers.)
- Start by configuring this "Servers" WSUS GPO exactly the same as your "Workstations" GPO.
- Then, under "Configure Automatic Updates", use Automatic Updating level 3 ("Auto download and notify for install") rather than 4 ("Auto download and schedule the install").
- Ensure "Target group name for this computer" is set to a distinct name, such as "Servers".
- Then ensure "Allow Automatic Updates immediate installation" is set to Disabled.
- Now set "Reschedule Automatic Updates scheduled installations" to Disabled.
- Finally, ensure "No auto-restart for scheduled Automatic Updates installations" is set to Enabled...just to be safe, even though we know it's only going to work half the time!
Apply this server-specific WSUS GPO to the OU where your servers are located. You will being to see servers appear in their own group in WSUS. (The group will be named whatever name you specified in step 4 above.) Once they are in that group, you can begin to see what updates are already installed and what updates need to be installed on each server.
When you decide to install a particular patch/update, you can simply approve it for your Servers group. WSUS will automatically upload the patch(es) to each server, but it will not install them. You will need to log in to each server and manually install the patches. That may seem like extra work, but it ensures that you control when the server reboots following applied updates.
Even though you have to manually do the actual install, WSUS is still helpful in this scenario for two reasons:
- It still automates the downloading of update files to each server from microsoft.com or WSUS -- this is still a huge time savings!
- WSUS gives you clear, comprehensive, up-to-the-minute data on what updates are installed on each server and what updates each server needs
We have operated in this framework in our organization for the past 6 months and have found it to be very successful.
09 January 2008
Some Advice About Inkjet Printers, Part 3
This is Part 3 of a three-part series of Tech Tips focusing on inkjet printers. If you missed Parts 1 and 2, click here to read from the beginning.
7. When buying an inkjet printer, consider a model that loads paper from the top.
Inkjet printers, like all other types of printers, load paper in different ways. The two predominant ways are from the top, like a typewriter, and from the bottom, like a photocopier. Although bottom-loading printers may be more aesthetically-pleasing, since the paper tray is underneath the printer and out-of-sight, the top-loading style has better long-term reliability.
Top-loading printers work with the force of gravity to pull the paper into the machine. Bottom-loading printers, on the other hand, have to pull sheets of paper against the force of gravity. The pulling is done by a series of rubber rollers. These rollers harden and lose their ability to grip the page over time, and they are usually first to fail on bottom-loading inkjet printers.
While rollers like these are a cost-effective and somewhat routine fix for laser printers, they are neither cost-effective nor routine for inkjet printers. If your bottom-loading inkjet printer begins to have trouble loading paper, its days are probably numbered. By comparison, a top-loading inkjet printer tends to see longer roller life, and even when the rollers wear out, gravity can help them along. You can often coax life out of a top-loading printer with failing rollers simply by "retrying" print jobs until the paper finally feeds, thanks to gravity. Bottom-loading printers do not have the same benefit.
8. When printing photos, brand of paper really does matter!
I mentioned earlier in this 3-part series that you do have a choice of brand when it comes to ink. However, if you plan to print high-quality photos (glossy or matte), you may be better off shelling out the money on the printer-brand ink and paper.
Yes, that's right: the brand of paper actually matters. I can't tell you what the physical differences are between brands of paper. I can't elaborate on the physics or chemistry of Epson ink and Canon paper. But I will offer a brief, marginally-thrilling true story as a word of caution.
Until not long ago, I owned a Canon inkjet printer capable of photo printing. In the early years, I always used Canon ink and Canon paper and found the photo results to be consistently impressive. While the colors on the photo that came out of the printer weren't exactly the same as those on the photo you saw on the screen, they were fairly close. Given that my monitor was never calibrated professionally, what you saw on the screen wasn't necessarily any less accurate than what you got on the page.
After a couple of years using the Canon and loving the photo output, I found a good deal on some generic photo paper at a computer show and brought some home. Guess what the results with the new paper were? Awful. The ink actually failed to sink into the page completely, instead pooling on top of the paper in big droplets. Unacceptable quality. I assumed that what I had was bargain-basement paper, and I got what I paid for.
Then about a year later, I picked up some Staples brand and some Kodak brand inkjet photo paper. Cue the printing problems a second time. Photos that looked great on the screen were coming out completely wrong on the page. Horribly wrong: green skin tones, oversaturation, overly-dark and under-contrasted colors. Even the Kodak paper yielded poor results no matter what printer settings I used. Painstakingly trying every photo paper setting and color processing setting in the Canon printer settings, nothing would work. I probably wasted an entire package of expensive photo paper and tens of dollars worth of ink trying to figure out what the problem was.
I thought for sure my printer was slowly dying, yet when I later when I tried again using Canon paper, the photos came out clear and accurate. It was then that I realized that I needed to purchase paper made by the same company that made my printer. I'm not sure if the poor results are the natural result when you disturb the delicate, engineered chemical balance between Canon ink and Canon paper, or simply another deliberate boardroom-hatched plot by Canon to force you to buy their expendables. Either way, if photos are what you're trying to make, you'll probably want to just shell out the extra bucks and save yourself a few headaches.
9. The best way to avoid all these inkjet headaches? Buy a laser printer. Seriously.
After reading three weeks of pure vitriol from me on the topic of inkjet printers, it should be no surprise to you that my final piece of advice to you is simple: avoid purchasing an inkjet printer if you can.
In the '80s and early '90s, those of us who had home computers used dot-matrix printers -- those noisy, slow printers that boasted lame features like "Near Letter Quality". They were the inexpensive home alternative to the expensive laser printers that were blossoming in the workplace. Late in the decade, inkjet printers took the baton from dot-matrix printers, offering silent operation, superior resolution, and even the ability to print photo-like images. At the time, inkjet printers were a boon for all of us, as laser printers were still prohibitively expensive for most home use.
In recent years, however, laser printers have come down so far in price that they now must be considered by any home user. The local big box store carries black-and-white laser printers for as little as $80, and color laser printers now can be found for as little as $250.
Think that a laser printer for your home PC is overkill? Think again:
- Laser printers are far more durable than inkjet printers. In my workplace, I can count several HP LaserJet 4 laser printers still in use today. These printers were manufactured circa 1994.....fourteen years ago.
- Laser toner cartridges cost more than inkjet ink cartridges, but they last many times longer. So much longer, in fact, that it is actually much cheaper, page for page, to print on a laser printer than on an inkjet printer. Need an example? We had an Epson Action Laser printer in our family that was purchased circa 1993. When I threw it away about 18 months ago, it was still working -- and more importantly, it was still on its original toner cartridge, more than a dozen years later! That one toner cartridge lasted so long that it long outlived its production run at Epson.
- Ask yourself if you really need color at home. If you don't do photo printing, you probably don't need it, and can find a B&W laser printer for about what you'd pay for an inkjet printer.
- Don't forget that laser printers reign supreme at printing text. Inkjet text printing has come a long way over the years, but laser text printing still looks as good as a page out of a textbook. Line drawings, sheet music, logos, and other vector-based artwork also look superior when printed out on a laser printer.
When my Canon inkjet printer finally died, I decided I'd had it with inkjet printers and made the leap to a color laser printer. After months of comparison shopping, I settled on the Brother HL-4070CDW. I couldn't be happier with it. Not only does it print the usual laser-sharp text and graphics, plus very good photos, but it is "fully-duplexed", allowing it to print on both sides of the page automatically. (A good idea for those of us trying to save a few trees...and a few dollars while we're at it.) The printer has a built-in network interface like most laser printers, but what really sets this one apart is that it also has a built-in wireless network interface. Now, I can locate this printer anywhere in my home that I want, and any computer in the house can print to it wirelessly. That's nice if you have a good-sized house and want to locate the printer in a central location like the kitchen, but your wireless router is upstairs in the home office.
In conclusion, while we all thought that computers would someday lead us to a paperless society, the proliferation of inkjet printers has only proven the opposite to be true. We like to make hard copies of what we see on the screen, and we like to make lots of them. But we don't often think about how much each page of printing costs us. So it's very important to take the time to buy the right printer for your PC.
Just remember this:

