You may not even know how to answer this question, given all the different types of security threats that all internet-connected computers face these days. PC security is more than a state of mind -- it's doing everything you can to protect yourself from people who want to hijack your computer, damage your data, and steal your personal information.
There are three key pieces of security software you need to have on your home computer:
ANTIVIRUS
ANTISPYWARE
FIREWALL
You may own one piece of software that accomplishes all 3 functions such as Norton Internet Security. Regardless, take the time to examine the security software you have installed on your PC. You may be leaving a gaping hole open to cybercriminals.
Here are some common pitfalls for home users, as well as some easy solutions.
1. Having antivirus software with no antispyware, or vice versa.
Once upon a time, all home users needed was antivirus software to ensure security. That was 10 years ago. Today, viruses may be the least of our threats. Adware and spyware can cripple a PC's resources and gather personal information about users. Some antivirus software applications have antispyware capabilities (and vice versa), but even those applications fall short in spyware detection.
A firewall, on the other hand, will protect you from live threats. There are lots of automated systems out there "sniffing" around, pinging random web addresses looking for an open hole into someone's computer. An "intrusion" into your system might even originate from deliberate human hacking. You need a firewall to shield your system from this hailstorm of attacks. A good firewall will not only tighten up all open network ports on your PC against incoming riff-raff, but it will scrutinize all outbound network traffic as well. That way, if adware or spyware on your PC tries to send data to a host site, the firewall will block this activity.
Adware, spyware, viruses, trojan horses......so many terms. There is one word that encompasses them all: malware. The best way for home users to protect themselves from malware is to install dedicated antivirus and anti-spyware and firewall software.
2. Relying on Windows Firewall as your sole firewall.
Windows XP and Vista both come with a rudamentary firewall as part of the operating system. While well-intentioned and not harmful for most home users, the efficacy of Windows Firewall is lame at best.
The best practice is to keep Windows Firewall enabled on your PC but install an additional software or hardware firewall for your system.
3. Letting the subscription expire on your security software.
Sure, you've got McAfee Antivirus and Trend Micro Antispyware software installed on your PC. No worries, right? Well, have you checked to see if your subscription is still active? It's important to keep your security software updated with the most up-to-the-minute malware information. Once the subscription expires, your security software will continue to run, but it will fail to detect the latest threats.
Open up each of your security applications and verify the expiration dates. You might want to make a note to yourself (perhaps an Outlook calendar appointment?) to renew your security software subscriptions right before they expire.
4. Ignoring security software because you're broke.
Hey, I get it. Antivirus costs $30, antispyware costs $30, and the firewall software might not even be included.
While there are many excellent commercial applications available, you can actually get decent protection without spending a dime. Here are a number of absolutely-free security applications:
ANTIVIRUS
- AVG Anti-Virus Free Edition
- Avast Home Edition 4.7
- Avira AntiVir PersonalEdition Classic
- PC Tools AntiVirus Free Edition 4.0
- Ad-Aware 2007
- Microsoft Windows Defender
- SpyBot Search and Destroy 1.4
- Trend Micro HijackThis 2.0.2
- SpywareBlaster 3.5.1
- Spyware Terminator 2.1
- AVG Anti-Rootkit (for Windows XP only)
Download and install any single application from each of the three categories if you don't have any protection. And don't be afraid to install more than one antispyware software at a time -- you can run multiple. Studies have shown that different antispyware applications catch different pieces of malware, so the more antispyware software you have installed, the greater your chances are complete protection.
5. Downloading from websites you haven't 100% verified.
You should know not to download anything from the internet unless you've verified the source. Even well-intentioned websites can carry infected software for download. Other websites are "spoofed", making you think that you're on a trusted site when in fact you're on an identical fake, feeding you malware and collecting your information.
Take the time to type in the exact address of the website you want up in the address bar of your internet browser. Sometimes simply doing a Google search for the website that you want yields spoof sites!
Also, avoid downloading and installing unnecessary software. But if you must, download it from a trusted, secure website such as http://www.download.com/ or http://www.pcworld.com/.
6. Using Internet Explorer, particularly versions 5 and 6.
Right, I know that the grand majority of internet users surf the web with some version of Microsoft's ubiquitous Internet Explorer. (Over 70% of you who visit my website use IE.) I'm not going to lie: I happen to be using it right now. There are websites that won't work correctly without it.
The problem is that all the criminal hackers in the world also know that 70% of you use IE. And that one fact makes IE a prime target for hacking.
Microsoft makes a decent attempt at trying to patch the security holes in IE, but the fact remains that a browser this popular is simply too big a target for hackers to find holes in. Although security patches come out on a regular basis from Microsoft (and you should always install them -- more on this below), they appear to be falling further and further behind in the cat-and-mouse game of browser security.
Fortunately, two of the best alternative browsers are free of charge: Mozilla's popular Firefox browser, and Opera Software's Opera Browser.
Why not give one of them a try? It only takes 5 minutes to download one of them, import all of your IE bookmarks into the new browser, and start surfing. You don't have to commit to using either of them permanently, and you can still run IE if you need to -- even simultaneously with Firefox or Opera. You may also notice a slight increase in browsing speed over IE, although I have not been able to verify this on either browser.
7. Not installing all the latest Windows Updates.
Microsoft Windows XP is still a work-in-progress, even as it approaches 7 years of age. (Windows Vista is more like a work-in-gestation!) It requires regular updates and patches from Microsoft to keep it as stable and secure as possible. Fortunately, Microsoft has automated this process for you. To ensure that you get regular updates, do the following:
- Right-click on My Computer and select Properties
- Select the Automatic Updates tab
- Ensure that the first option is selected: Automatic (recommended)
- Click OK
When new updates are automatically downloaded by your computer from the Microsoft website, a yellow shield will appear in the lower-right corner of your screen:
 Click on it! A dialog box will then ask you if you want to install updates. Say yes! The updates will begin to install themselves. You may be required to restart your computer at the end of this process.
Click on it! A dialog box will then ask you if you want to install updates. Say yes! The updates will begin to install themselves. You may be required to restart your computer at the end of this process.You can also manually verify that your computer is completely up to date:
- Go to the Start and select All Programs
- Select either Microsoft Update or Windows Update
An IE window will pop up that will take you to a special Microsoft website that checks your PC for installed updates. Follow the on-screen instructions to determine if your PC needs additional Windows updates.

 Then a dialog box will pop up....just click the OK button:
Then a dialog box will pop up....just click the OK button: 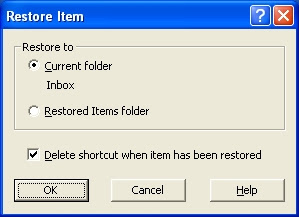
 Consider using Enterprise Vault instead of your Personal Folders to store your messages! Unlike Personal Folders, Enterprise Vault uses Outlook Web Access, gets backed up frequently, and is far more crash-proof and corruption-proof.
Consider using Enterprise Vault instead of your Personal Folders to store your messages! Unlike Personal Folders, Enterprise Vault uses Outlook Web Access, gets backed up frequently, and is far more crash-proof and corruption-proof.